What is Azure Application Gateway Web Application Firewall (WAF)?
Web applications are increasingly target of malicious attacks that exploit commonly known vulnerabilities, such as SQL injection and cross site scripting attacks. Preventing such exploits in the application requires rigorous maintenance, patching, and monitoring at multiple layers of the application topology. A centralized web application firewall (WAF) protects against web attacks and simplifies security management without requiring any application changes. Application and compliance administrators get better assurance against threats and intrusions.
Azure Application Gateway is an umbrella term for a virtual appliance that provides application delivery control (ADC) as a platform as a service (PaaS) in Azure. It offers various layer 7 load-balancing capabilities for your applications. This service is highly available, scalable, and fully managed by Azure.
Features
Application Gateway supports
- Autoscaling,
- SSL offloading, and end-to-end SSL,
- A web application firewall (WAF),
- Cookie-based session affinity,
- URL path-based routing,
- Multisite hosting, and host of other features.
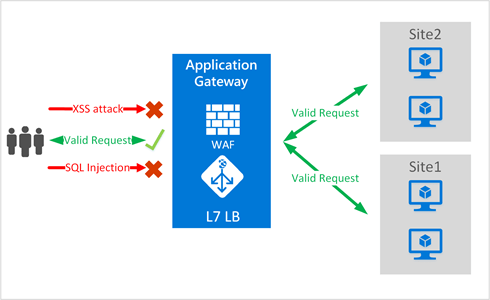
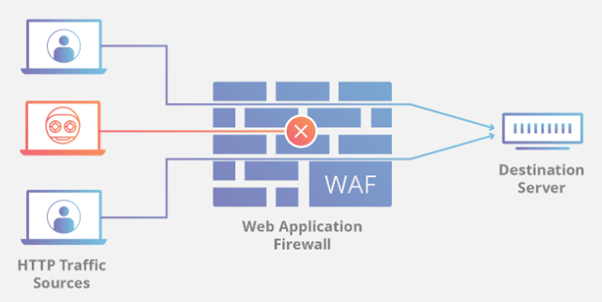
A WAF or Web Application Firewall helps protect web applications by filtering and monitoring HTTP traffic between a web application and the Internet. It typically protects web applications from attacks such as cross-site forgery, cross-site-scripting (XSS), file inclusion, and SQL injection, among others.
In order to properly shield your web applications, you need a Web Application Firewall (WAF). Unlike a traditional firewall, a WAF does not provide perimeter protection for the entire enterprise. It is a highly specialized security tool specifically designed to protect web applications, not the servers. A WAF actually resides at the outer edge of your network in front of the public side of a web application and analyses incoming traffic.
Web Application Firewall integrated with Application Gateway’s core offerings further strengthens the security portfolio and posture of applications protecting them from many of the most common web vulnerabilities, as identified by Open Web Application Security Project (OWASP) top 10 vulnerabilities. Application Gateway WAF comes pre-configured with OWASP ModSecurity Core Rule Set (3.0 or 2.2.9), which provides baseline security against many of these vulnerabilities. With simple configuration and management, Application Gateway WAF provides rich logging capabilities and selective rule enablement.
Features
Web Application Firewall protects the site from:
- SQL-injection protection.
- Cross-site scripting protection.
- Protection against other common web attacks, such as command injection, HTTP request smuggling, HTTP response splitting, and remote file inclusion.
- Protection against HTTP protocol violations.
- Protection against HTTP protocol anomalies, such as missing host user-agent and accept headers.
- Protection against crawlers and scanners.
- Detection of common application misconfigurations (for example, Apache and IIS).
- Configurable request size limits with lower and upper bounds.
- Exclusion lists let you omit certain request attributes from a WAF evaluation. A common example is Active Directory-inserted tokens that are used for authentication or password fields.
- Create custom rules to suit the specific needs of your applications.
- Geo-filter traffic to allow or block certain countries from gaining access to your applications.
- Protect your applications from bots with the bot mitigation rule set.
Benefits
Following are the core benefits that Web Application Firewall on Application Gateway provides:
Protection
- Protect your web applications from web vulnerabilities and attacks without modification to back-end code.
- Protect multiple web applications at the same time. An instance of Application Gateway can host of up to 40 websites that are protected by a web application firewall.
- Create custom WAF policies for different sites behind the same WAF
- Protect your web applications from malicious bots with the IP Reputation ruleset (preview).
Monitoring
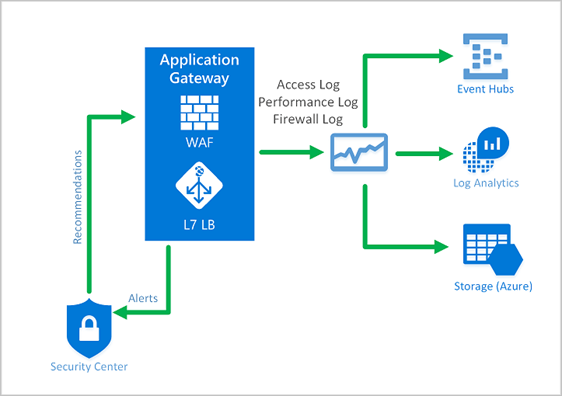
- Monitor attacks against your web applications by using a real-time WAF log. The log is integrated with Azure Monitor to track WAF alerts and easily monitor trends.
- The Application Gateway WAF is integrated with Azure Security Center. Security Center provides a central view of the security state of all your Azure resources.
Customization
- Customize WAF rules and rule groups to suit your application requirements and eliminate false positives.
- Associate a WAF Policy for each site behind your WAF to allow for site-specific configuration
- Create custom rules to suit the needs of your application
WAF Policy
To enable a Web Application Firewall on an Application Gateway, you must create a WAF Policy. This Policy is where all of the managed rules, custom rules, exclusions, and other customizations such as file upload limit exist.
Core rule sets
Application Gateway supports three rule sets: CRS 3.1, CRS 3.0, and CRS 2.2.9. These rules protect your web applications from malicious activity.
Custom rules
Application Gateway also supports custom rules. With custom rules, you can create your own rules, which are evaluated for each request that passes through WAF. These rules hold a higher priority than the rest of the rules in the managed rule sets. If a set of conditions is met, an action is taken to allow or block.
WAF modes
The Application Gateway WAF can be configured to run in the following two modes:
- Detection mode: Monitors and logs all threat alerts. You turn on logging diagnostics for Application Gateway in the Diagnostics You must also make sure that the WAF log is selected and turned on. Web application firewall doesn’t block incoming requests when it’s operating in Detection mode.
- Prevention mode: Blocks intrusions and attacks that the rules detect. The attacker receives a “403 unauthorized access” exception, and the connection is closed. Prevention mode records such attacks in the WAF logs.
Anomaly Scoring mode
OWASP has two modes for deciding whether to block traffic: Traditional mode and Anomaly Scoring mode.
In Traditional mode, traffic that matches any rule is considered independently of any other rule matches. This mode is easy to understand. But the lack of information about how many rules match a specific request is a limitation. So, Anomaly Scoring mode was introduced. It’s the default for OWASP 3.x.
In Anomaly Scoring mode, traffic that matches any rule isn’t immediately blocked when the firewall is in Prevention mode. Rules have a certain severity: Critical, Error, Warning, or Notice. That severity affects a numeric value for the request, which is called the Anomaly Score. For example, one Warning rule match contributes 3 to the score. One Critical rule match contributes 5.
| TABLE 1 | |
| Severity | Value |
| Critical | 5 |
| Error | 4 |
| Warning | 3 |
| Notice | 2 |
There’s a threshold of 5 for the Anomaly Score to block traffic. So, a single Critical rule match is enough for the Application Gateway WAF to block a request, even in Prevention mode. But one Warning rule match only increases the Anomaly Score by 3, which isn’t enough by itself to block the traffic.
WAF monitoring
Monitoring the health of your application gateway is important. Monitoring the health of your WAF and the applications that it protects are supported by integration with Azure Security Centre, Azure Monitor, and Azure Monitor logs.
For implementation of Azure Application Gateway with WAF, please Click HERE.
